Mergers and acquisitions (M&A) are often viewed as one of the most strategic ways to gain market share, acquire cutting-edge technologies, expand geographical reach, or eliminate competition. Companies frequently enter into these transactions with high hopes of synergy and growth. However, many acquisitions have failed, leaving companies with damaged reputations, financial losses, and operational turmoil. Understanding why these high-profile mergers go wrong can provide valuable lessons for future business strategies.
Why High-Stakes Acquisitions Go Wrong

So, why do mergers and acquisitions fail? Despite the promise of accelerated growth and competitive advantage, many acquisitions fail to live up to their expectations. These deals often come with hidden complexities that aren't immediately apparent during the initial stages. As a result, companies may struggle to realize the projected benefits and instead face unexpected financial, operational, and cultural hurdles.
The Illusion of Synergy
A common belief in M&A is that combining two businesses will lead to synergistic benefits, such as cost savings, increased market power, or enhanced innovation. In practice, these synergies are often difficult to realize. Many acquisitions are driven by optimism, assuming the mere combination of operations will result in greater efficiencies. However, synergies rarely come to fruition when companies fail to integrate their cultures, strategies, and systems truly. Often, business units clash, resulting in operational inefficiencies, employee dissatisfaction, and, ultimately, wasted resources.
Moreover, some deals are based on overly optimistic financial forecasts that fail to account for the complexities of post-merger integration. As a result, the expected "win-win" outcome can often turn into a costly misstep.
The Pressure to Close
In high-stakes mergers, the pressure to finalize deals quickly is immense. Executives and investors may push for rapid closures, believing this will avoid competitors' risk of capitalizing on the opportunity. This rush can lead to significant flaws in the decision-making process. In some cases, companies close deals without fully understanding the financial, operational, or cultural challenges involved. This haste may result in overlooking red flags, underestimating integration costs, or misjudging market conditions. The outcome is often a deal completed on paper but ultimately fails in execution.
Integration: The Most Overlooked Phase
The integration phase is the most critical but often the most neglected aspect of M&A. While the focus is often placed on completing the transaction, the real work begins after the deal is done. Integrating two companies requires a comprehensive strategy to align operations, consolidate teams, harmonize technology platforms, and merge corporate cultures. The deal can fall apart if integration is not carefully planned and executed. Issues such as employee turnover, lack of coordination between departments, and conflicting business philosophies can lead to inefficiency, reducing the value of the acquisition and leaving both companies struggling.
Ten Business Acquisitions That Backfired Spectacularly
These high-profile failures demonstrate that even the most well-funded and promising acquisitions can go awry. While each case is unique, common factors such as poor integration, misalignment of business strategies, and cultural clashes often emerge as key drivers of failure. Understanding these lessons can help future acquirers avoid similar pitfalls and make more informed decisions. Here are the worst acquisitions of all time.
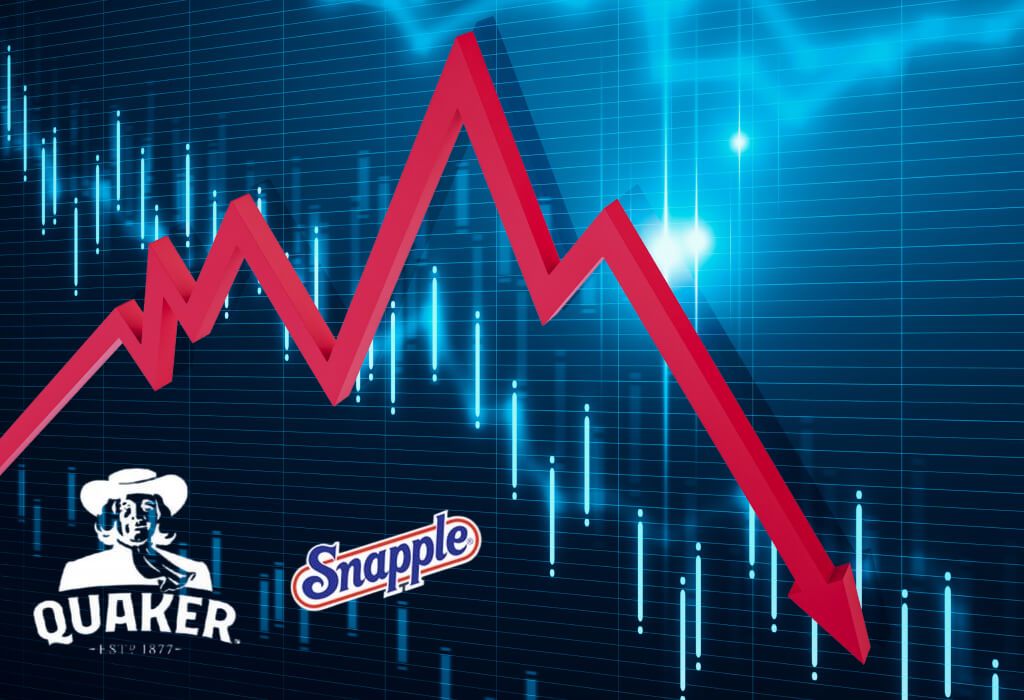
Quaker Oats Buying Snapple (1994)
Quaker Oats acquired Snapple for $1.7 billion, hoping to replicate its success with Gatorade. However, the deal was poorly executed, and Quaker struggled to integrate Snapple into its portfolio. Distribution problems, mismatched marketing strategies, and a lack of alignment between the brands plummeted Snapple's value. After just 27 months, Quaker sold Snapple for $300 million, a massive loss of nearly $1.4 billion.
Daimler and Chrysler Merger (1998)
Daimler-Benz and Chrysler merged in 1998 in a deal worth $36 billion, hailed as equals. However, the cultural divide between the German and American automakers was vast. Daimler's focus on precision engineering clashed with Chrysler's emphasis on innovation and design. The integration process was riddled with difficulties, and in 2007, Daimler sold Chrysler at a significant loss, marking one of the most infamous failures in automotive history.
AOL and Time Warner (2000)
AOL's $165 billion acquisition of Time Warner during the dot-com boom is often cited as one of the worst mergers in history. The merger was fueled by the optimism surrounding the internet's potential. However, it became clear that AOL's internet-based business model could not be seamlessly integrated with Time Warner's traditional media operations. Internal conflicts, slow revenue growth, and changes in the media landscape left the combined entity struggling. Eventually, the merger was unwound, and AOL was sold for a fraction of its original valuation.
eBay's Acquisition of Skype (2005)
eBay purchased Skype for $2.6 billion with the aim of enhancing communication between buyers and sellers. However, the lack of strategic fit between eBay's core business and Skype's communications platform led to failure. The acquisition proved to be a poor match, and eBay eventually sold Skype in 2009, having written down over $1 billion of its value.
HP's Purchase of Autonomy (2011)
Hewlett-Packard (HP) acquired Autonomy, a UK-based software company, for $11.1 billion. However, HP's acquisition was marred by accounting irregularities. Due to Autonomy's inflated value and poor integration, the company took an $8.8 billion impairment charge. The aftermath caused a significant loss in HP's credibility and a blow to its financial stability.
Google's Motorola Mobility Acquisition (2012)
Google's $12.5 billion purchase of Motorola Mobility was aimed at bolstering its position in the smartphone market. While the acquisition was initially seen as a move to gain patents for Android, the smartphone division underperformed, and Google was forced to sell Motorola to Lenovo in 2014 for $2.91 billion. Despite holding onto valuable patents, Google lost billions in the deal.
Microsoft Acquiring Nokia's Devices Unit (2014)
Microsoft acquired Nokia's phone business for $7.2 billion, hoping to revive its position in the mobile market. However, integration issues and a decline in the smartphone market meant the acquisition did not provide the expected benefits. Microsoft eventually wrote off billions and laid off thousands of employees to restructure the business.
Amazon's Acquisition of Whole Foods (2017)
Amazon's acquisition of Whole Foods for $13.7 billion marked the company's entry into the brick-and-mortar grocery business. While the acquisition increased Amazon's footprint in the retail space, the integration was slower than expected. Whole Foods struggled to adapt to Amazon's data-driven and technology-oriented approach, which ultimately slowed the anticipated transformation of the grocery industry.
SoftBank's Acquisition of WeWork Stake (2019)
SoftBank invested heavily in WeWork, even attempting to rescue the company after its failed IPO. The company's valuation plummeted due to governance issues, unsustainable business models, and poor leadership. SoftBank's eventual control over WeWork didn't yield the expected returns, and the company has struggled with restructuring ever since.
Teladoc's Merger with Livongo (2020)
Teladoc's merger with Livongo for $18.5 billion in 2020 was seen as an important move in the telemedicine industry. However, as market conditions changed and competition increased, the synergy that was expected from the merger did not materialize. Teladoc's stock price declined, leading to doubts about the long-term value of the deal.
What These Deals Teach Us

The failures outlined above offer crucial insights into the risks inherent in high-stakes acquisitions. They underscore the importance of thorough due diligence, realistic expectations, and meticulous integration planning. By learning from these mistakes, companies can approach future deals with a more strategic and measured mindset, ultimately improving their chances of success.
Assumptions Are the Enemy of Strategy
The failed mergers and acquisitions above demonstrate that assumptions, rather than hard data, can undermine an M&A strategy. Companies tend to make optimistic assumptions about future growth, synergy, and integration, but these assumptions can become costly mistakes without thorough analysis.
Operational Complexity Is Where Most Deals Break
While financials and market conditions are important, the true challenge of an acquisition lies in aligning operations, technologies, and cultures. Operational integration can often be more complex than anticipated, and without a clear plan, companies face delays, inefficiencies, and internal conflicts.
Speed Without Precision Is a Risk Multiplier
While the pressure to close a deal quickly can be compelling, rushing through the due diligence and integration phases can lead to significant risks. A deal made hastily without careful consideration often ends up being more expensive than taking the time to ensure everything is aligned.
Key Frameworks for Smarter Acquisition Decisions
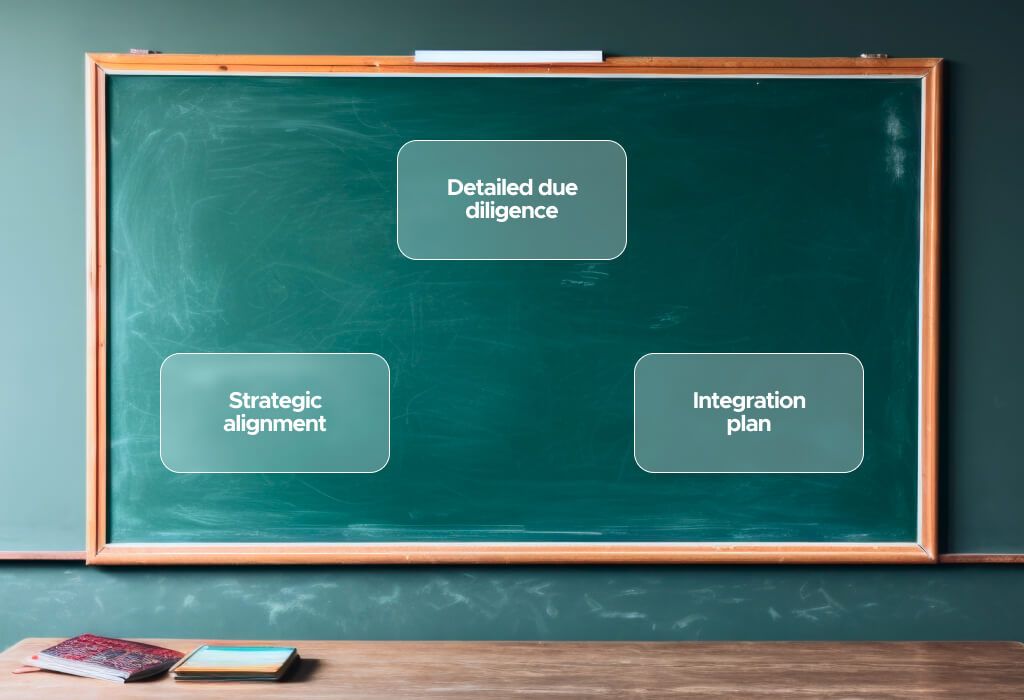
By adhering to these frameworks, businesses can approach acquisitions with a structured, informed mindset that mitigates common risks. Strategic fit analysis ensures that the target company aligns with long-term goals, while layered due diligence uncovers potential issues before the deal is finalized. Finally, a robust integration plan guarantees that both organizations work seamlessly together.
Before the Deal: Strategic Fit Analysis
It is essential to thoroughly evaluate whether the potential acquisition fits the company's long-term goals. It involves examining market overlap, evaluating technological compatibility, and assessing the cultural fit of both organizations.
During the Deal: Layered Due Diligence
Due diligence should be multi-layered, including financial audits, market analysis, and regulatory checks. This way, companies can identify potential pitfalls and avoid rash decisions based on incomplete information.
After the Deal: Integration Architecture
Deals succeed or fail in the integration phase. A well-defined plan that includes leadership alignment, clear communication, and accountability mechanisms is crucial. Without this, even the best-executed deal can result in wasted potential and financial loss.
Conclusion
While mergers and acquisitions can be highly beneficial, they come with substantial risks. The worst tech mergers and acquisitions above show that the key to success lies in the financials and careful planning, thorough due diligence, and strategic integration. For businesses looking to make smarter acquisition decisions, it is crucial to approach these deals with a clear vision, a detailed strategy, and the willingness to invest in proper execution. Boundeal is a reliable merger partner ready to provide high-quality transaction support.