Corporate data breaches represent a critical risk to organizations, their clients, and the broader economy. These cyberattacks compromise sensitive data, halt business operations, and undermine confidence in affected entities. Often involving millions or billions of records, breaches expose personal information, financial details, and trade secrets. The consequences include massive financial damages, legal disputes, and long-term reputational harm. This article explores the most significant corporate data breaches, evaluates their effects, identifies key takeaways, and provides actionable strategies to safeguard data and prevent future incidents.
Understanding Data Breaches
A data breach occurs when unauthorized parties gain access to protected or confidential digital information. Attackers exploit vulnerabilities such as outdated software, weak authentication, or human oversight to extract data like names, emails, payment details, or passwords. Common tactics include phishing, malware, hacking, or insider misconduct. Breaches result in financial penalties, legal challenges, and loss of customer trust for businesses, while individuals risk identity theft and financial fraud.
The Most Significant Corporate Data Breaches in History
Corporate data breaches transcend mere technical failures, reshaping trust, regulations, and security practices. These incidents expose vulnerabilities, cost billions, and redefine how businesses protect sensitive information. Below are the most impactful breaches, detailing their scope, consequences, and lessons for modern cybersecurity.
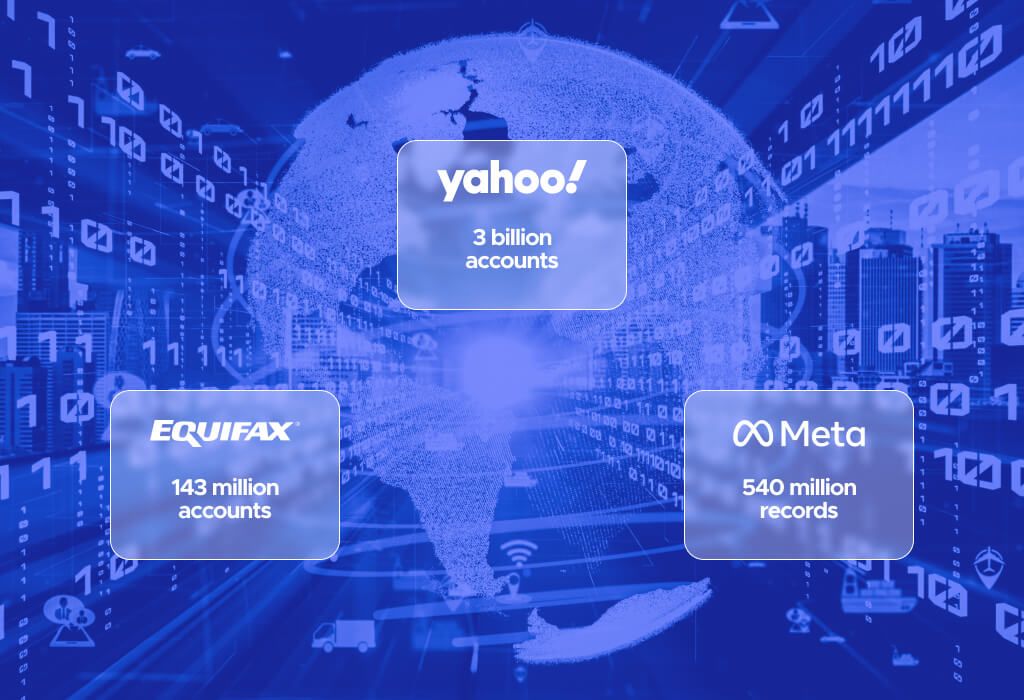
Yahoo (2013–2014) – 3 Billion Accounts
The Yahoo breach remains the largest by account volume, marking a historic cybersecurity failure. Between 2013 and 2014, hackers infiltrated all 3 billion Yahoo accounts, stealing names, emails, phone numbers, hashed passwords, and security questions. Undetected until 2016, the breach slashed $350 million from Yahoo’s sale to Verizon and triggered widespread criticism of its outdated encryption and slow response.
Alibaba (2019) – 1.1 Billion Data Points
Alibaba’s 2019 breach exposed critical weaknesses in third-party oversight. A developer scraped 1.1 billion data points from Taobao, including usernames, mobile numbers, and purchase records, over eight months. The incident, not involving passwords, still highlighted the dangers of unmonitored API access and lax controls on data scraping within e-commerce ecosystems.
LinkedIn (2021) – 700 Million Profiles
LinkedIn’s 2021 breach showcased the risks of exploiting public data. Cybercriminals scraped 700 million user profiles—92% of its base—extracting names, emails, phone numbers, and job details via API vulnerabilities. Though no passwords were compromised, the incident fueled debates about the sensitivity of “public” data and the ease of bot-driven exploitation.
Equifax (2017) – 147 Million Individuals
Equifax’s 2017 breach devastated trust in credit reporting agencies. Hackers exploited an unpatched Apache Struts flaw, accessing Social Security numbers, birth dates, and credit card details of 147 million people. Costing $1.4 billion in settlements, the breach spurred legislative changes and underscored the critical need for timely software updates.
Meta (2019) – 540 Million Records
Meta’s 2019 breach revealed flaws in third-party data handling. A partner app left 540 million user records—IDs, names, and interactions—exposed on public servers. While no passwords were leaked, the incident highlighted Meta’s limited control over external data, prompting calls for stricter oversight of third-party access.
Marriott International (2014–2018) – 500 Million Guests
Marriott’s breach, spanning 2014 to 2018, exposed integration risks during acquisitions. Hackers accessed Starwood’s reservation system, stealing names, passport numbers, and credit card data of 500 million guests. Discovered post-acquisition, the breach led to a $123 million GDPR fine and emphasized robust due diligence in mergers.
Target (2013) – 110 Million Shoppers
Target’s 2013 breach exposed supply chain vulnerabilities. Hackers used stolen HVAC vendor credentials to steal credit cards and personal data from 110 million customers. Costing $252 million, the incident accelerated the adoption of EMV chips and stricter vendor security protocols across retail.
Adobe (2013) – 153 Million Accounts
Adobe’s 2013 breach set a precedent for encryption failures. Attackers stole 153 million email addresses, weakly encrypted passwords, and source code, impacting the software security industry-wide. The incident drove Adobe to revamp its security and sparked calls for stronger encryption standards.
MySpace (2013) – 360 Million Accounts
MySpace’s 2013 breach, revealed in 2016, proved legacy data remains a target. Hackers accessed 360 million accounts, extracting emails and poorly hashed passwords. The leak, risking identity theft via reused credentials, highlighted the need to secure outdated platforms.
First American Financial (2019) – 885 Million Documents
First American’s 2019 exposure showed basic security lapses. A web flaw left 885 million records—bank details, Social Security numbers, and mortgages—publicly accessible without authentication. The breach triggered lawsuits and exposed the dangers of inadequate access controls in finance.
JPMorgan Chase (2018) – 83 Million Accounts
JPMorgan Chase’s 2018 breach signaled escalating financial cyber threats. Hackers used a compromised employee login to access the names and emails of 83 million clients, though no financial data was stolen. Doubling its cybersecurity budget, JPMorgan’s response set a model for banking sector defenses.
MOVEit Transfer (2023) – 93 Million Records
The 2023 MOVEit breach exemplified modern supply chain risks. The Cl0p gang exploited a zero-day flaw in MOVEit software, impacting 93 million records across 2,700 organizations. The rapid global attack emphasized proactive vulnerability management and third-party software scrutiny.
Key Lessons Learned from Major Data Breaches

The most significant corporate data breaches weren’t just technical failures — they were systemic lapses in governance, oversight, and preparedness. From financial giants to tech platforms, each case offers hard-earned lessons. Below are key takeaways that businesses of all sizes should internalize.
The Cost of Complacency
Too many organizations learn the hard way that “if it isn’t broken, don’t fix it” doesn’t apply to cybersecurity. Seemingly minor oversights like ignoring patches or failing to monitor unusual activity can spiral into historic breaches.
In both Yahoo’s and Marriott’s cases, attackers lurked in systems for years undetected, compromising hundreds of millions of users and costing billions in damage control and reputation loss. Complacency invites catastrophe. Regular vulnerability scans, timely patching, and automated system monitoring must be built into business-as-usual operations, not just activated in crisis mode. A culture of proactive security is a company’s first and strongest line of defense.
Regulatory Fallout and Class Action Lawsuits

When a data breach occurs, legal and financial consequences often follow close behind. Global privacy regulations such as the GDPR, CCPA, and PCI-DSS enforce strict accountability, and failing to comply is costly.
Equifax’s 2017 breach resulted in over $1.4 billion in fines, settlements, and mandated security upgrades. Marriott’s mishandling of guest data under GDPR led to a fine of £99 million (≈$123 million). But beyond official penalties, companies also face class action lawsuits, shareholder backlash, and steep recovery costs. In this landscape, compliance isn’t just a box-ticking exercise; it’s a foundation for resilience. Organizations must invest in legal audits, maintain clear data processing documentation, and ensure that privacy protections are not only deployed but also demonstrable.
Importance of Vendor and Insider Risk Management
Not all breaches originate from malicious hackers; many stem from trusted connections. Third-party vendors, former employees, and even careless staff members can inadvertently open the door.
Target’s 2013 breach originating from credentials stolen via an HVAC vendor is now a textbook case of supply chain vulnerability. Similarly, the Facebook 2019 leak involved third-party apps storing data insecurely on public servers. Organizations must implement zero-trust architectures, enforce the principle of least privilege (PoLP) access, and audit third-party integrations continuously. Insider training is just as vital: phishing simulations, awareness campaigns, and role-specific security protocols help close the human gap.
The Need for Rapid Response
Speed can mean the difference between a contained breach and a full-scale crisis. Yet, too many companies lack the playbooks and tools to act decisively under pressure.
In the Yahoo and Marriott breaches, attackers had years to roam undetected, giving them ample time to exfiltrate data and deepen their foothold. Such delays amplify exposure, regulatory penalties, and remediation costs. Every company should have a tested incident response plan, which includes real-time detection systems, cross-functional response teams, and secure communication channels. Regular breach simulations (“tabletop exercises”) help teams rehearse high-stakes decision-making before disaster strikes.
Best Practices for Data Security
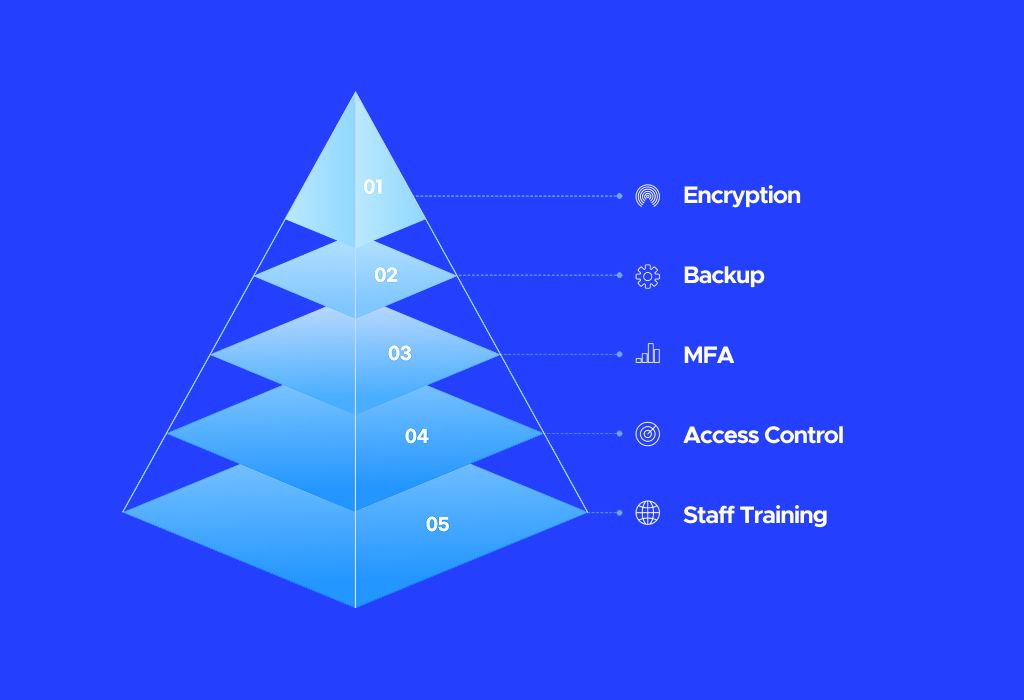
In today’s digital landscape, protecting sensitive information requires more than just a single security tool or policy. Effective data security hinges on a comprehensive, multi-layered strategy that combines technology, processes, and people. The following best practices form the cornerstone of a resilient defense against increasingly sophisticated cyber threats:
Encrypt All Sensitive Data. Encryption transforms readable data into an unreadable format without the correct decryption key, ensuring that even if attackers access data, it remains useless.
Patch Systems and Software Promptly. Unpatched software creates easy entry points for cybercriminals. Many high-profile breaches exploit known vulnerabilities for which patches were available but not applied.
Conduct Regular Security Audits. Security audits, both internal and external, help organizations identify weak spots, misconfigurations, and compliance issues before they lead to breaches.
Train Staff to Identify Phishing, Malware, and Social Engineering
Humans remain one of the weakest links in cybersecurity. Attackers use phishing emails, fake phone calls, and social engineering tactics to trick employees into revealing credentials or installing malware.
Use Strict Access Controls. Limiting data access to only those who absolutely need it minimizes exposure if an account is compromised. Role-based access control (RBAC), multi-factor authentication (MFA), and the principle of least privilege ensure that users can only obtain information necessary for their roles.
Monitor Networks in Real Time for Unusual Activity. Real-time network monitoring and intrusion detection systems (IDS) enable early detection of anomalies that may indicate a breach, such as unusual login attempts or data transfers.
Back-Up Data Regularly. Data backups are a critical safety net. In case of ransomware attacks or data loss, having reliable, recent backups ensures business continuity and quick recovery.
Test Incident Response Plans. Having an incident response plan is essential, but it must be tested regularly through drills and simulations to ensure teams can execute it effectively under pressure.
Implementing these best practices is not just a technical necessity; it is a critical business imperative. In an environment where cyber threats evolve rapidly and data breaches can lead to severe financial, legal, and reputational damage, a proactive and layered approach to data security is the best defense.
Why Boundeal VDR Is Built for Leak-Proof Corporate Collaboration

Boundeal VDR delivers a secure virtual data room for corporate collaboration. It offers end-to-end encryption, granular access controls, and real-time monitoring to block leaks. Built for due diligence, mergers, acquisitions, and sensitive projects, it ensures data stays protected. Features include audit trails, secure file sharing, and compliance support, fostering trust and safety in business dealings. Boundeal VDR stands as a reliable shield against the rising tide of cyber threats.